转自:https://mp.weixin.qq.com/s/UI-abxv9g603ERCrNR2G4A
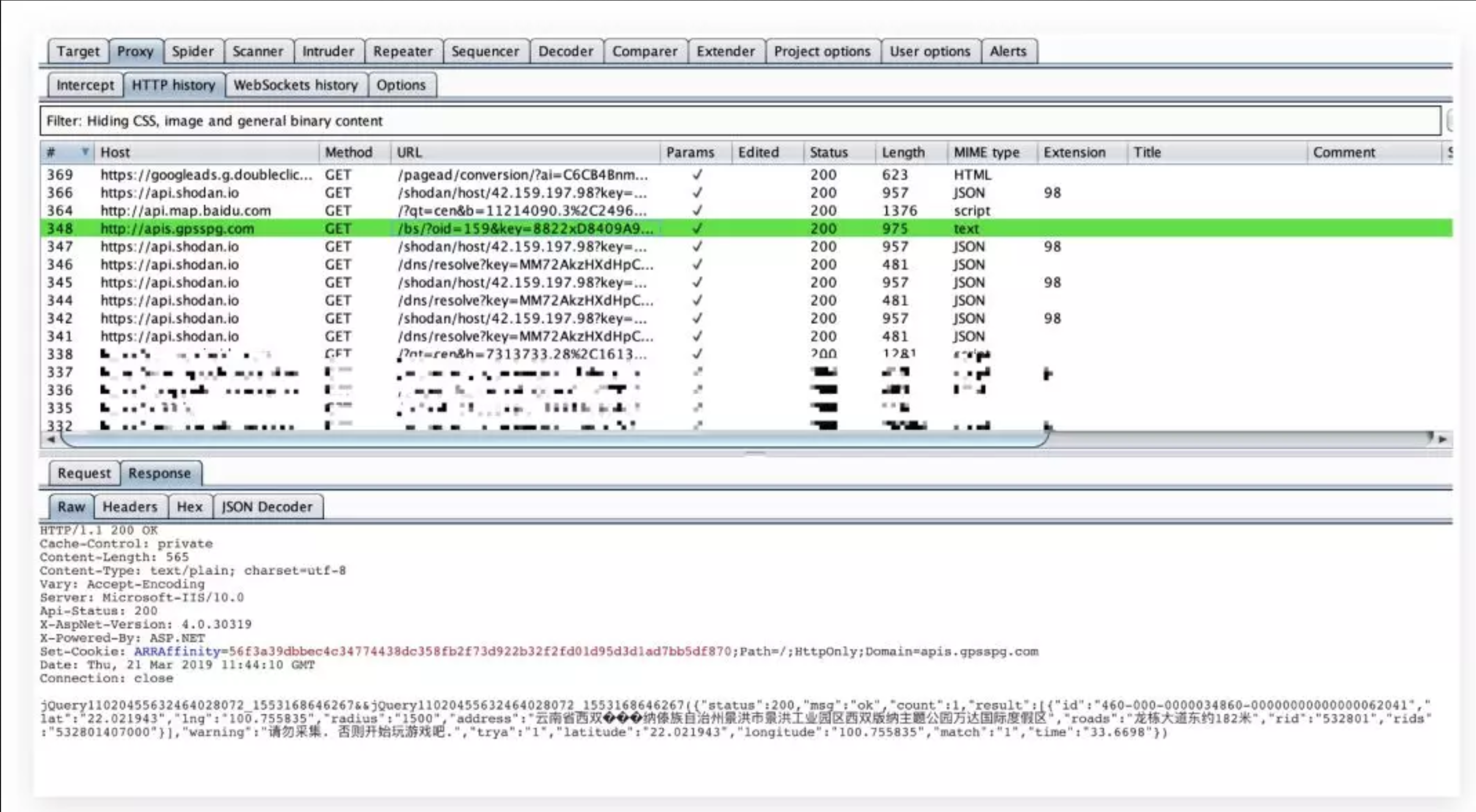
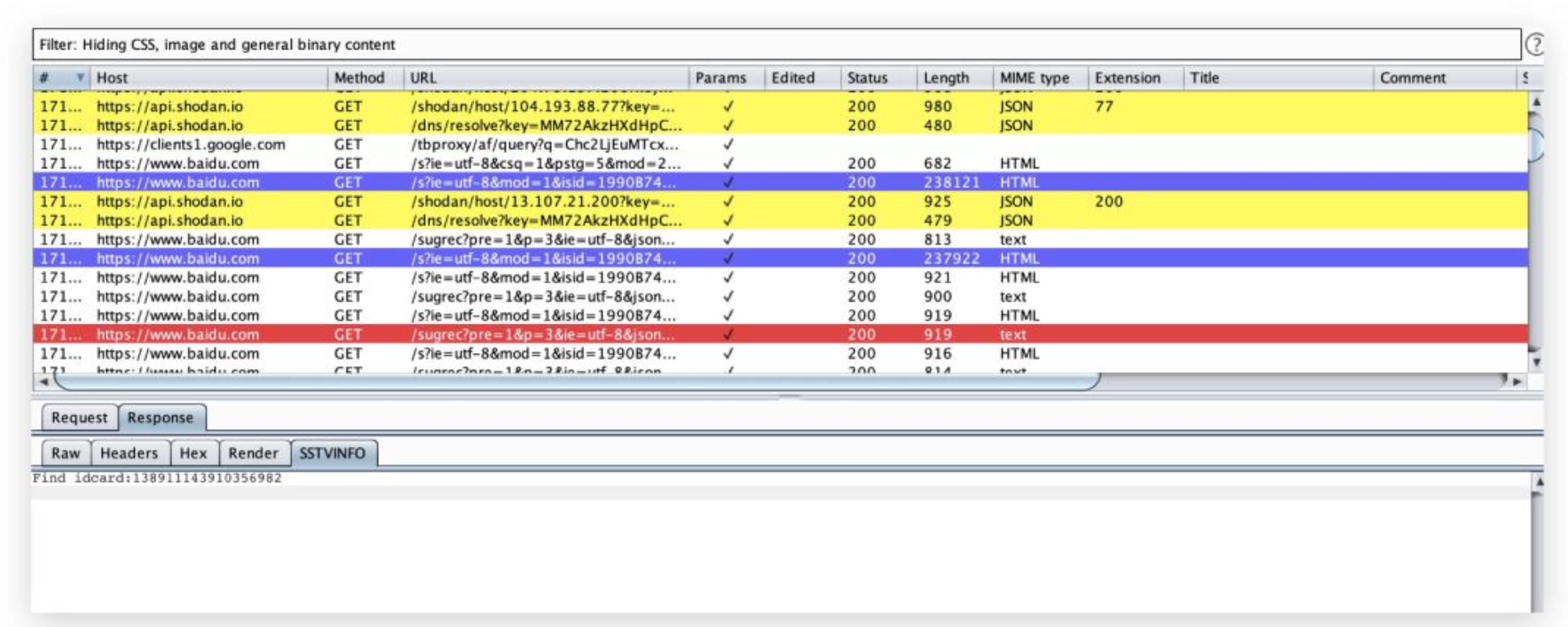
在挖SRC的过程中敏感信息泄漏是最常见的漏洞之一,但有时我们可能经常会忽略掉一些重要的数据包。因此我们针对Burp编写了一款标记敏感信息的插件,会自动将代理模块中包含敏感信息的数据包标记出来。
有了它,妈妈再也不会担心我挖洞漏掉敏感信息啦!
更新日志:
支持标记身份证信息
支持标记手机号信息
支持标记经纬度信息
修复手机号误报
删除json格式化功能
增加标记IP信息功能
添加INFO标签功能
使用效果:
下载地址:
https://github.com/nian-hua/BurpExtender
Version
1.3
Dependencies
burp
re
关键代码:
1、电话号码判断
def stringIsPhone(string):
iphones = re.findall(r'[%"\'< ](?:13[012]\d{8}[%"\'< ]|15[56]\d{8}[%"\'< ]|18[56]\d{8}[%"\'< ]|176\d{8}[%"\'< ]|145\d{8}[%"\'< ]|13[456789]\d{8}[%"\'< ]|147\d{8}[%"\'< ]|178\d{8}[%"\'< ]|15[012789]\d{8}[%"\'< ]|18[23478]\d{8}[%"\'< ]|133\d{8}[%"\'< ]|153\d{8}[%"\'< ]|189\d{8}[%"\'< ])', string)
if iphones != []:
iphones = set(iphones)
iphoneSet = set()
for i in iphones:
iphoneSet.add(filter(str.isdigit, i))
iphones = ','.join(iphoneSet)
return iphones
return False
2、GPS经纬度信息
def stringIsGps(Xhacker, string): # check GPS information
if Xhacker:
return False
if ("\"longitude\"" in string and "\"latitude\"" in string) or ("\"lat\"" in string and "\"lon\"" in string):
locations = re.findall(r'\d{2,3}\.\d{3,6}', string)
for location in locations:
if 3 < float(location) < 135:
return location
return False
3、身份证信息
def stringIsIdCard(string):
coefficient = [7, 9, 10, 5, 8, 4, 2, 1, 6, 3, 7, 9, 10, 5, 8, 4, 2]
parityBit = '10X98765432'
idcards = re.findall(r'([1-8][1-7]\d{4}[1|2]\d{3}[0|1]\d{1}[1-3]\d{4}[0-9|X|x])', string)
idcardSet = set()
if idcards != []:
for idcard in idcards:
sumnumber = 0
for i in range(17):
sumnumber += int(idcard[i]) * coefficient[i]
if parityBit[sumnumber % 11] == idcard[-1]:
idcardSet.add(idcard)
idcards = ','.join(idcardSet)
return idcards
return False
4、IP地址信息
def stringIsAssets(string):
assets = re.findall(r'\b(?:(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\.){3}(?:25[0-5]|2[0-4][0-9]|[01]?[0-9][0-9]?)\b', string)
if assets != []:
assetss = set(assets)
assetsSet = set()
for i in assets:
assetsSet.add(i)
assetss = ','.join(assetsSet)
return assetss
return False
转载请注明:jinglingshu的博客 » Burp敏感信息插件V2.0