一、背景
opensca主要功能是分析软件成分,根据组件版本号进行匹配,输出对应组件存在的安全漏洞。但是实际应急过程中有时候也会出现组件投毒应急的威胁情况,会有特定版本受到影响,但是开源版默认是不支持此风险分析的。
目前想到的解决思路一:修改本地的数据库文件,增加自定义扫描规则,如此便可以解决(后期可以一直使用,但需要重新扫描项目)
思路二:自定义一个数据库,解析扫描后的组件资产,进行查询输出(可用于离线环境)
思路三:自定义一个数据库,写一个查询脚本利用saas平台的接口进行查询(用于可联网环境)
这里列举下思路三的实现方案
二、实现思路
例如此投毒风险预警:
文章来源:https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw
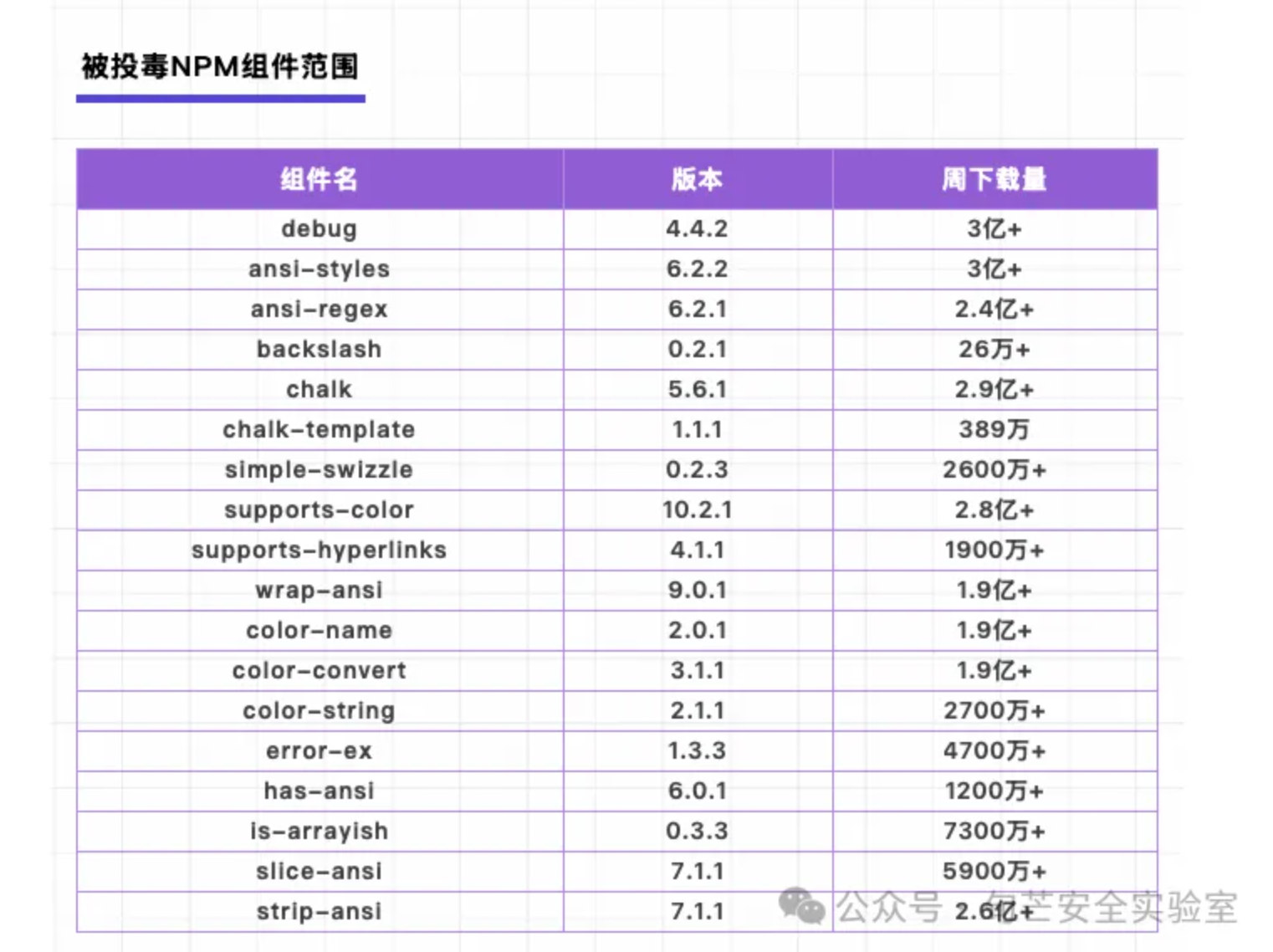
将上述受影响版本,自定义为数据库db.json 用于存储存在问题组件
[
{
"component": "debug",
"version": "4.4.2",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "ansi-styles",
"version": "6.2.2",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "ansi-regex",
"version": "6.2.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "backslash",
"version": "0.2.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "chalk",
"version": "5.6.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "chalk-template",
"version": "1.1.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "simple-swizzle",
"version": "0.2.3",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "supports-color",
"version": "10.2.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "supports-hyperlinks",
"version": "4.1.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "wrap-ansi",
"version": "9.0.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "color-name",
"version": "2.0.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "color-convert",
"version": "3.1.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "color-string",
"version": "2.1.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "error-ex",
"version": "1.3.3",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "has-ansi",
"version": "6.0.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "is-arrayish",
"version": "0.3.3",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "slice-ansi",
"version": "7.1.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
},
{
"component": "strip-ansi",
"version": "7.1.1",
"description": "qix开发者账号泄漏导致NPM仓库超大规模投毒",
"reference_link": "https://mp.weixin.qq.com/s/dODGqn0GP17LDZys3Mh5mw",
"info_time": "2025-09-09"
}
]
利用接口组件资产查询功能,进行组件查询
<code><span class="code-snippet__attribute">GET</span> /oss-saas/api-v1/asset/component?componentName=debug&pageNum=<span class="code-snippet__number">1</span>&pageSize=<span class="code-snippet__number">10</span> HTTP/<span class="code-snippet__number">1</span>.<span class="code-snippet__number">1</span></code>
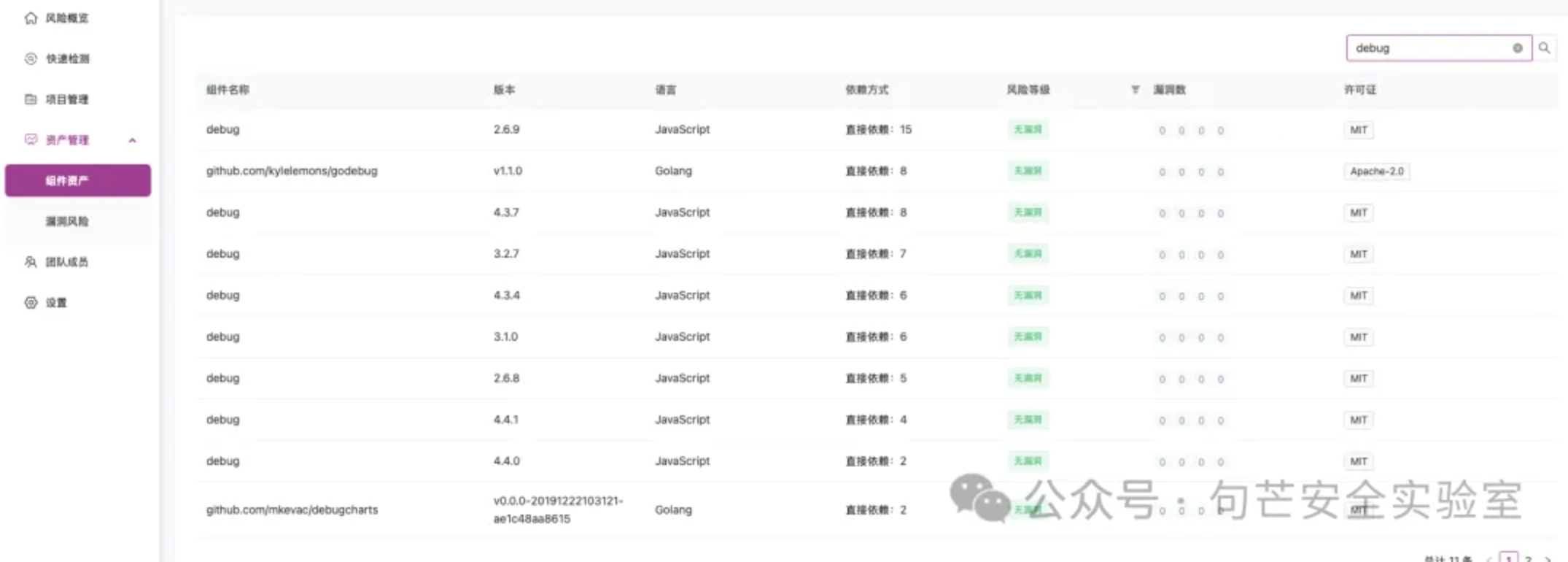
利用关联分析接口获取受影响的项目
GET /oss-saas/api-v1/asset/component/xxxx HTTP/1.1
编写脚本,记得替换token
import json
import requests
# Authorization替换为你的token
HEADERS = {
"Host": "opensca.xmirror.cn",
"Authorization": "xxx",
"User-Agent": "Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:142.0) Gecko/20100101 Firefox/142.0",
"Accept": "application/json, text/plain, */*"
}
BASE_URL = "https://opensca.xmirror.cn/oss-saas/api-v1/asset"
def process_components():
# 1. 读取db.json文件
with open('db.json', 'r') as f:
components = json.load(f)
results = []
for comp in components:
# 2. 查询组件接口
search_url = f"{BASE_URL}/component?componentName={comp['component']}&pageNum=1&pageSize=10"
search_resp = requests.get(search_url, headers=HEADERS)
if search_resp.status_code != 200:
print(f"组件查询失败: {comp['component']} - HTTP {search_resp.status_code}")
continue
search_data = search_resp.json().get('data', {})
# 3. 匹配版本并获取ID
matched_ids = []
for record in search_data.get('records', []):
if record.get('version') == comp['version']:
print(f"发现受影响组件: {comp['component']}@{comp['version']} -> ID: {record['id']}")
matched_ids.append(record['id'])
# 4. 获取受影响的project
for comp_id in matched_ids:
detail_url = f"{BASE_URL}/component/{comp_id}"
detail_resp = requests.get(detail_url, headers=HEADERS)
if detail_resp.status_code != 200:
print(f"组件详情查询失败: ID {comp_id} - HTTP {detail_resp.status_code}")
continue
detail_data = detail_resp.json().get('data', {})
# 5. 提取项目信息
for project in detail_data.get('vulnImpactProject', []):
result = {
"projectName": project['projectName'],
"component": comp['component'],
"version": comp['version'],
"description": comp['description'],
"reference_link": comp['reference_link']
}
results.append(result)
print("发现受影响项目: " + ", ".join([
f"项目: {result['projectName']}",
f"组件: {result['component']}",
f"版本: {result['version']}"
]))
# 6. 输出最终结果
print("\n最终审计结果:如果为空则表示未发现,有会直接输出项目名")
for res in results:
print(f"| {res['projectName']} | {res['component']}@{res['version']} | {res['description']} | {res['reference_link']} |")
if __name__ == "__main__":
process_components()
三、最终结果
这里实际受影响的debugb版本为:4.4.2 我的项目下没有受影响的就修改为正在用的版本做演示展示
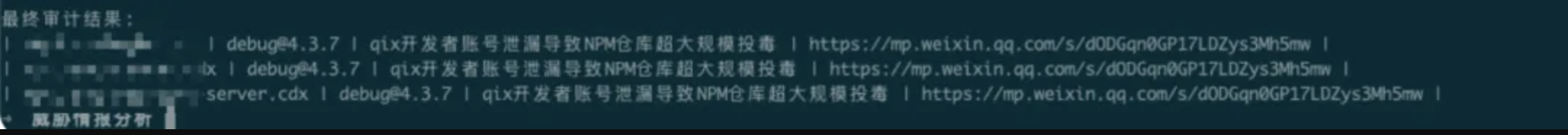
没有发现有风险的项目输出如下:
转自:https://mp.weixin.qq.com/s/uGAmONPNUvFohrX-aR5rJQ?mpshare=1&scene=1&srcid=1008PC78x0tbJJJaNggNbna8&sharer_shareinfo=31ac8c4b4bc96141d313ecfdc875e317&sharer_shareinfo_first=31ac8c4b4bc96141d313ecfdc875e317&version=5.0.0.99730&platform=mac#rd